Analysis of the Buschtrommel Trojan
Magnus MischelIntroduction
It was brought to my attention that Buschtrommel is one of the latest trojans that will disable security software such as anti-trojan programs and firewalls. After analyzing it as I always do with new trojans so that they can be added to the TrojanHunter database, I thought it might be a good idea to post the results here. Some new things came up, and I thought it best to let everyone know about them.To begin with, here is a short excerpt from the Buschtrommel readme file (translated from german):
Well, nothing new here. BioNet 3.12 did the same thing. Could this trojan have something else up its sleeve?Buschtrommel Version: Beta 2 Written by Natok Introduction ~~~~~~~~~~~~ This tool was created to demostrate the weaknesses of firewalls. It should be used for educational purposes only and the author assumes no responsibility for what you do with it.
To create some bait for the trojan, I installed The Cleaner 3.2 on a fresh installation of Windows 98 and then made two copies of notepad.exe, naming them avp32.exe and frw.exe to simulate anti-virus software (KAV) and a firewall (ConSeal PC Firewall). After setting up some logging facilities I started the trojan server. Immediately upon running the file, The Cleaner and my two copies of Notepad died. A result of the trojan using TerminateProcess, no doubt.
KAV, ConSeal and The Cleaner... What More?
To find out what software the trojan targets, I decided to take a look at what readable strings lurked inside the trojan server executable. The file was packed with a popular executable packer (UPX), so I had to unpack it to be able to take a peek inside. Searching for strings, the following came up as highly suspicious:305425: _AVP32.EXE 305445: _AVPCC.EXE 305465: _AVPM.EXE 305485: AVP32.EXE 305505: AVPCC.EXE 305525: AVPM.EXE 305545: AVP.EXE 305633: NAVAPW32.EXE 305657: NAVW32.EXE 305781: ICLOAD95.EXE 305805: ICMON.EXE 305825: ICSUPP95.EXE 305849: ICLOADNT.EXE 305873: ICSUPPNT.EXE 305961: IFACE.EXE 306065: ANTS.EXE 306085: guard.EXE 306105: fast.EXE 306189: Anti-Trojan.exe 306285: iamapp.exe 306305: iamserv.exe 306389: FRW.EXE 306477: blackice.exe 306501: blackd.exe 306516: SVW3 306593: zonealarm.exe 306617: vsmon.exe 306721: WrCtrl.exe 306741: WrAdmin.exe 306853: cleaner3.exe 306877: cleaner.exe 306897: tca.exe 306913: MooLive.exe 306997: lockdown2000.exe 307089: Sphinx.exe 307173: tfak.exe 307297: VSHWIN32.EXE 307321: VSECOMR.EXE 307341: WEBSCANX.EXE 307365: AVCONSOL.EXE 307389: VSSTAT.EXE 337829: Try to kill Firewalls and Anti-Vir tools.. 337893: Software\McAfee\McAfee Firewall\CurrentVersion\McAfee Firewall 337965: Warn:Allow Everything 337997: Warn:Block Everything 338029: McAfee Firewall disabled 338077: McAfee Firewall enabled 338113: *KILLAVP* 338133: *KILLNAV* 338153: *KISOPO* 338173: *KILLANTS* 338193: *KILLANTITROJAN* 338221: *KILLPANDA* 338241: ATKILL 338257: CONSEALKILL 338277: ICEKILL 338293: ZONEKILL 338313: WRKILL 338329: *KILLCLEAN* 338349: *KIMACA* 338369: *KISPHINX* 338389: *KILLTFAK* 338409: *LOCKKILL* 338441: Software\WRQ\IAM\FirewallState 338481: FilterEnabled 338505: At Guard disabled 338533: SPHINX 338549: Software\Biodata\SPHINX 338581: Sphinx found. 338617: Software\WRQ\IAM\Installation Info 338661: Path 338677: At Guard : 338697: ZONE 338713: Software\Zone Labs\ZoneAlarm 338777: Zone Alarm Version : 338809: CONSEAL 338825: Software\Signal 9 Solutions\ConSeal PC FIREWALL 338881: InstallPath 338901: Conseal : 338921: CLEAN3 338937: Software\MooSoft Development\The Cleaner 338989: install_dir 339009: Cleaner3 : 339041: Software\TinySoftware\WinRoute 339081: InstDir 339097: Tiny Software : 339125: *NIS?* 339141: Software\Symantec\InstalledApps 339181: Norton Internet Security 339217: NIS : 339233: *NFS01* 339249: system\CurrentControlSet\Services\VxD\VNETSUP 339317: FileSharing 339337: ATI01 339353: IcmpFilterEnabled 339381: At Guard ICMP disabled 339413: ATI011 339429: At Guard ICMP enabled 339461: ATI02 339477: Software\WRQ\IAM\Filters 339513: All Filters 339533: At Guard Filters disabled 339569: ATI022 339585: At Guard Filters enabled 339621: ATI03 339637: FilterLearningModeEnabled 339673: At Guard learning mode disabled 339713: ATI033 339729: At Guard learning mode enabled 340101: BLACKAUTO 340121: Network ICE/BlackICE/RemoveAutoRun.BAT 340169: Black ICE Autorun disabled 340205: Black ICE not found 340233: STOPBLACK 340253: Network ICE/BlackICE/StopBlackd.BAT 340297: Black ICE stopped 340325: BLACKLOG0 340345: Network ICE/BlackICE/blackice.ini 340389: disabled 340409: packetLog.logging 340437: Packet Logging 340461: Packet Logging disabled 340493: BLACKLOG1 340513: enabled 340529: Packet Logging enabled 340561: BLACKTRACE0 340581: backTrace.nbnodestatus 340613: Back Trace 340633: Traceing disabled 340661: BLACKTRACE1 340681: Traceing enabled 340709: ICQ_NOT 340737: \SOFTWARE\Microsoft\Registry\Settings 340785: KeyTime 340801: ICQ Notify enabled 340829: ICQ_OFF 340845: ICQ Notify disabled 340873: *NIS01* 340913: Software\Symantec\IAM\FirewallState 340957: BlockIGMP 340977: *NIS02* 340993: ICMPFilterEnabled 341021: *NIS03* 341037: Software\Symantec\IAM\Filters 341077: Filter Manager 341101: *NIS04* 341117: *NIS05* 341133: Software\Symantec\IAM\HTTPConfig 341177: FilterAds 341197: *NIS06* 341213: FilterExecutable 341241: *NIS07* 341257: FilterHTTP 341277: *NIS08* 341293: FilterPrivacy 341317: *NIS09* 341333: FilterPrivacyBrowse 341361: *NIS10* 341377: FilterPrivacyCookie 341405: *NIS11* 341421: BlockIPFragments 341449: *NIS12* 341465: DatagramReceiveAction 341497: *NIS13* 341513: CookieAssistand 341537: *NIS14* 341553: ExecutableAssistand 341581: *ANT01* 341597: Software\e-brainstorm\ANTS 2.0\ 341637: IF3-Engine 341657: *ANT02* 341673: Trojan First Aid Kit 341705: *ANT03* 341721: Heuristik 341741: *ANT04* 341757: Nachfragen 341777: *ANT05* 341793: Sofort 341809: *ANT06* 341837: *ANT07* 341865: *ANT08* 341881: Modified 341901: *ANT09* 341917: Alle Scannen 341941: *ANT?* 341957: ANTS 2.0 installed 341985: ANTS 2.0 not found 342013: CLEAN? 342029: CLEAN5 342045: Software\MooSoft Development\The Cleaner\Options 342105: autoscan 342125: Autoscan disabled 342153: CLEAN51 342169: Autoscan enabled 342197: CLEAN1 342213: scanzips 342233: Scan ZIPs disabled 342261: CLEAN11 342277: Scan ZIPs enabled 342305: CLEAN2 342321: scanstealth 342341: Stealth Scan disabled 342373: CLEAN21 342389: Stealth Scan enabled 342421: tcastartup 342441: TCAstartup disabled 342469: CLEAN31 342485: TCAstartup enabled 342513: CLEAN4 342529: ignore0 342545: Cleaner ignoresQuite an impressive list, wouldn't you say? All of the strings are related to firewalls and anti-virus/anti-trojan programs. These include Innoculate-IT, BlackICE, Norton Internet Security, ANTS, The Cleaner and McAfee Firewall, to name a few. What worried me more is that the list seemed to include the registry keys related to the configuration entries for these applications, for example
Software\MooSoft Development\The Cleaner\Options. What could the trojan be needing these for? I was determined to find out at this point...
The Trojan Client
Thinking now is as good a time as any to start the trojan client, I went ahead and did just that.
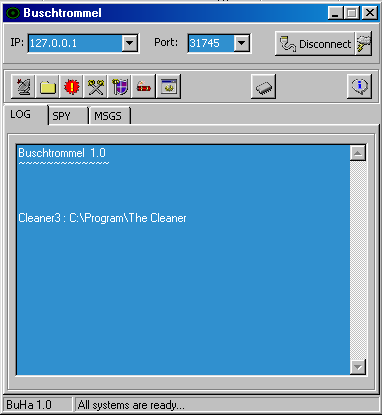
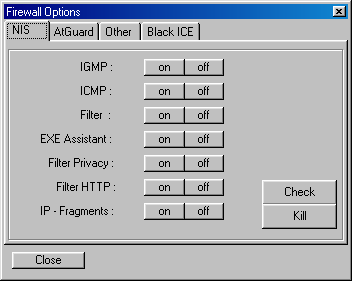
As you can see, the trojan server has let the client know that it found The Cleaner installed on the compromised system. What strikes you when you look at the toolbar of the trojan client are the two buttons with the tool-tips "Firewall Settings" and "Anti-Virus Settings". Below are screenshots of the windows that pop up when you click "Firewall Settings" and "Anti-Virus Settings", respectively.
 |
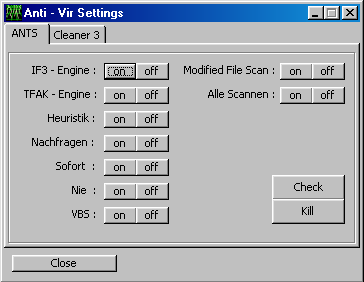 |
What you can see when you look at the screenshots is that the trojan lets you remotely change the settings of the anti-virus/anti-trojan programs and firewalls. For example, take a look at the below "Cleaner" tab of the Anti-Virus control center of Buschtrommel:
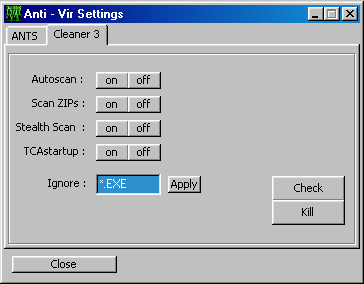
Do you notice the label saying "Ignore" and the edit-box next to it? Guess what happens when you press "Apply"? That's right, the trojan will write a setting to the registry that will make The Cleaner ignore files with the extension .exe. After this setting has been applied, The Cleaner will happily skip the scanning of any trojan server files. Similar things can be achieved with the settings of other security software. You can tell firewalls to let the trojan communication take place or simply kill them so that they aren't running at all. All while the user doesn't have a clue that this is going on and thinks he is well protected by his firewall.
 Buy Now
Buy Now